Cybersecurity researchers have detailed a new campaign that likely targets entities in Southeast Asia with a previously unrecognized Linux malware that's engineered to enable remote access to its operators, in addition to amassing credentials and function as a proxy server. The malware family, dubbed "FontOnLake" by Slovak cybersecurity firm ESET, is said to feature … [Read more...] about Researchers Warn of FontOnLake Rootkit Malware Targeting Linux Systems
Researchers
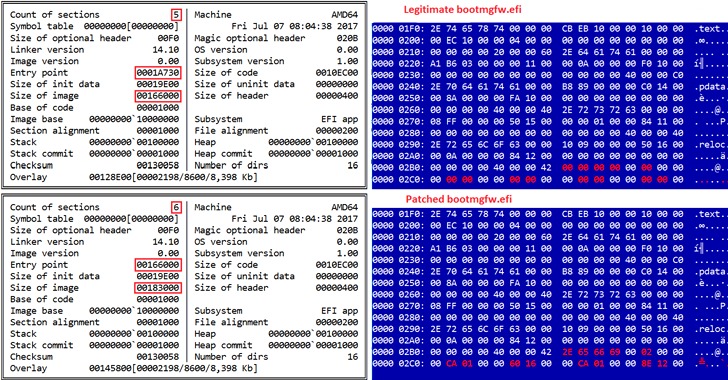
Researchers Discover UEFI Bootkit Targeting Windows Computers Since 2012
Cybersecurity researchers on Tuesday revealed details of a previously undocumented UEFI (Unified Extensible Firmware Interface) bootkit that has been put to use by threat actors to backdoor Windows systems as early as 2012 by modifying a legitimate Windows Boot Manager binary to achieve persistence, once again demonstrating how technology meant to secure the environment prior … [Read more...] about Researchers Discover UEFI Bootkit Targeting Windows Computers Since 2012
Researchers Find New Evidence Linking Diavol Ransomware to TrickBot Gang
Cybersecurity researchers have disclosed details about an early development version of a nascent ransomware strain called Diavol that has been linked to threat actors behind the infamous TrickBot syndicate. The latest findings from IBM X-Force show that the ransomware sample shares similarities to other malware that has been attributed to the cybercrime gang, thus establishing … [Read more...] about Researchers Find New Evidence Linking Diavol Ransomware to TrickBot Gang
Researchers Warn of Linux Cryptojacking Attackers Operating from Romania
A threat group likely based in Romania and active since at least 2020 has been behind an active cryptojacking campaign targeting Linux-based machines with a previously undocumented SSH brute-forcer written in Golang. Dubbed "Diicot brute," the password cracking tool is alleged to be distributed via a software-as-a-service model, with each threat actor furnishing their own … [Read more...] about Researchers Warn of Linux Cryptojacking Attackers Operating from Romania
China’s New Law Requires Researchers to Report All Zero-Day Bugs to Government
The Cyberspace Administration of China (CAC) has issued new stricter vulnerability disclosures regulations that mandate security researchers uncovering critical flaws in computer systems to mandatorily disclose them first-hand to the government authorities within two days of filing a report. The "Regulations on the Management of Network Product Security Vulnerability" are … [Read more...] about China’s New Law Requires Researchers to Report All Zero-Day Bugs to Government
Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to alter a document's visible content by displaying malicious content over the certified content without invalidating its signature. "The attack idea exploits the flexibility of PDF certification, which allows signing or adding annotations to … [Read more...] about Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
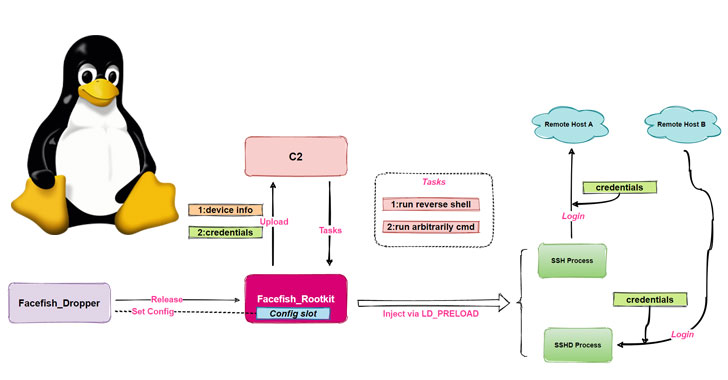
Researchers Warn of Facefish Backdoor Spreading Linux Rootkits
Cybersecurity researchers have disclosed a new backdoor program capable of stealing user login credentials, device information and executing arbitrary commands on Linux systems. The malware dropper has been dubbed "Facefish" by Qihoo 360 NETLAB team owing its capabilities to deliver different rootkits at different times and the use of Blowfish cipher to encrypt communications … [Read more...] about Researchers Warn of Facefish Backdoor Spreading Linux Rootkits
Researchers Uncover Iranian State-Sponsored Ransomware Operation
Iran has been linked to yet another state-sponsored ransomware operation through a contracting company based in the country, according to new analysis. "Iran's Islamic Revolutionary Guard Corps (IRGC) was operating a state-sponsored ransomware campaign through an Iranian contracting company called 'Emen Net Pasargard' (ENP)," cybersecurity firm Flashpoint said in its findings … [Read more...] about Researchers Uncover Iranian State-Sponsored Ransomware Operation
Researchers Find Additional Infrastructure Used By SolarWinds Hackers
The sprawling SolarWinds cyberattack which came to light last December was known for its sophistication in the breadth of tactics used to infiltrate and persist in the target infrastructure, so much so that Microsoft went on to call the threat actor behind the campaign "skillful and methodic operators who follow operations security (OpSec) best practices to minimize traces, … [Read more...] about Researchers Find Additional Infrastructure Used By SolarWinds Hackers
Researchers uncover a new Iranian malware used in recent cyberattacks
An Iranian threat actor has unleashed a new cyberespionage campaign against a possible Lebanese target with a backdoor capable of exfiltrating sensitive information from compromised systems. Cybersecurity firm Check Point attributed the operation to APT34, citing similarities with previous techniques used by the threat actor as well as based on its pattern of victimology. APT34 … [Read more...] about Researchers uncover a new Iranian malware used in recent cyberattacks