It is a time when many are thinking of their families and loved ones, time off work, and gift-giving – the holidays. However, while many have their minds outside the realm of work during the holiday season, often, this is when attackers plan their most sinister attacks. So how can you take precautions to protect your organization during these times? Why holidays put your … [Read more...] about Why Holidays Put Your Company at Risk of Cyber Attack (And How to Take Precautions)
risk
Navigating Vendor Risk Management as IT Professionals
One of the great resources available to businesses today is the large ecosystem of value-added services and solutions. Especially in technology solutions, there is no end to the services of which organizations can avail themselves. In addition, if a business needs a particular solution or service they don't handle in-house, there is most likely a third-party vendor that can … [Read more...] about Navigating Vendor Risk Management as IT Professionals
Minimize Risk and Impact with a Security Platform Approach
Much has been written about the Sunburst attack, a supply chain attack using the SolarWinds Orion application. Many organizations are still diligently working to understand the potential exposure to their organization from this devastating attack. And many are starting to think about how they can get to a future state where the risk of these type of attacks are minimized. So … [Read more...] about Minimize Risk and Impact with a Security Platform Approach
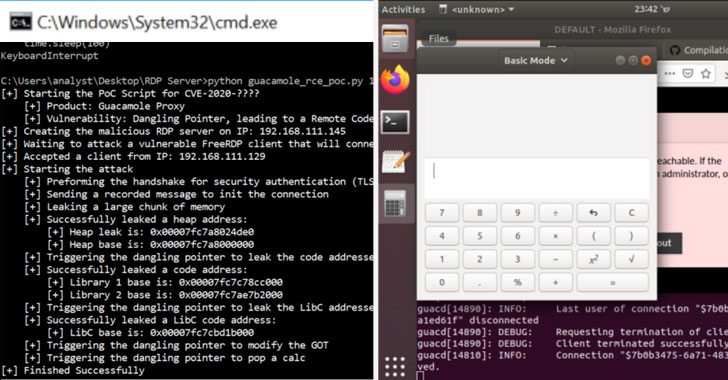
Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking
A new research has uncovered multiple critical reverse RDP vulnerabilities in Apache Guacamole, a popular remote desktop application used by system administrators to access and manage Windows and Linux machines remotely.The reported flaws could potentially let bad actors achieve full control over the Guacamole server, intercept, and control all other connected … [Read more...] about Critical Apache Guacamole Flaws Put Remote Desktops at Risk of Hacking
Ripple20: Critical Vulnerabilities Might be Putting Your IoT/OT Devices at Risk
Cybersecurity researchers from JSOF have just published a set of 19 vulnerabilities, dubbed Ripple20 that are impacting the TCP/IP stack developed by Treck. This software stack is integrated into millions of systems used in the healthcare, transportation, manufacturing, telecoms and energy markets, potentially affecting a very large number of organizations and critical … [Read more...] about Ripple20: Critical Vulnerabilities Might be Putting Your IoT/OT Devices at Risk
New Ripple20 Flaws Put Billions of Internet-Connected Devices at Risk of Hacking
The Department of Homeland Security and CISA ICS-CERT today issued a critical security advisory warning about over a dozen newly discovered vulnerabilities affecting billions of Internet-connected devices manufactured by over 500 vendors across the globe.Dubbed "Ripple20," the set of 19 vulnerabilities resides in a low-level TCP/IP software library developed by Treck, which, if … [Read more...] about New Ripple20 Flaws Put Billions of Internet-Connected Devices at Risk of Hacking
How SMBs Can Mitigate the Growing Risk of File-based Attacks
Cases of document-based malware are steadily rising. 59 percent of all malicious files detected in the first quarter of 2019 were contained in documents.Due to how work is done in today's offices and workplaces, companies are among those commonly affected by file-based attacks. Since small to medium businesses (SMBs) usually lack the kind of security that protects their larger … [Read more...] about How SMBs Can Mitigate the Growing Risk of File-based Attacks