Apr 02, 2025Ravie LakshmananCloud Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that could have allowed a malicious actor to access container images and even inject malicious code. "The vulnerability could have allowed such an identity to abuse its Google … [Read more...] about Google Fixed Cloud Run Vulnerability Allowing Unauthorized Image Access via IAM Misuse
Run
Falcon Cloud Security Supports Google Cloud Run to Strengthen Serverless Application Security
We’re thrilled to share that the CrowdStrike Falcon® sensor now fully supports Google Cloud Run, bringing advanced security capabilities to your serverless applications. While we announced this at Google Cloud Next in April 2024, this blog goes deeper into the integration and shares how customers leveraging Google Cloud Run and CrowdStrike can deploy Falcon quickly to enhance … [Read more...] about Falcon Cloud Security Supports Google Cloud Run to Strengthen Serverless Application Security
Three CISOs Share How to Run an Effective SOC
Sep 06, 2023The Hacker NewsSecurity Operations Center (SOC) The role of the CISO keeps taking center stage as a business enabler: CISOs need to navigate the complex landscape of digital threats while fostering innovation and ensuring business continuity. Three CISOs; Troy Wilkinson, CISO at IPG; Rob Geurtsen, former Deputy CISO at Nike; and Tammy Moskites, Founder of … [Read more...] about Three CISOs Share How to Run an Effective SOC
WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
Aug 19, 2023THNMalvertising / Website Security Cybersecurity researchers have detailed an updated version of an advanced fingerprinting and redirection toolkit called WoofLocker that's engineered to conduct tech support scams. The sophisticated traffic redirection scheme was first documented by Malwarebytes in January 2020, leveraging JavaScript embedded in compromised … [Read more...] about WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
Researchers Find Potential Way to Run Malware on iPhone Even When it’s OFF
A first-of-its-kind security analysis of iOS Find My function has identified a novel attack surface that makes it possible to tamper with the firmware and load malware onto a Bluetooth chip that's executed while an iPhone is "off." The mechanism takes advantage of the fact that wireless chips related to Bluetooth, Near-field communication (NFC), and ultra-wideband (UWB) … [Read more...] about Researchers Find Potential Way to Run Malware on iPhone Even When it’s OFF
How to Run Google SERP API Without Constantly Changing Proxy Servers
You've probably run into a major problem when trying to scrape Google search results. Web scraping tools allow you to extract information from a web page. Companies and coders from across the world use them to download Google's SERP data. And they work well – for a little while. After several scrapes, Google's automated security system kicks in. Then it kicks you out. The … [Read more...] about How to Run Google SERP API Without Constantly Changing Proxy Servers
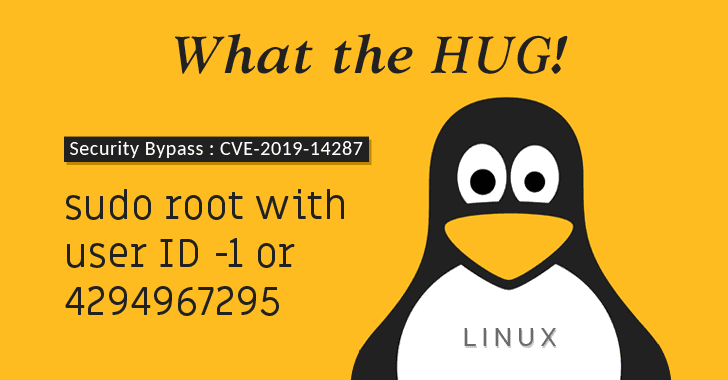
Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted
Attention Linux Users!A new vulnerability has been discovered in Sudo—one of the most important, powerful, and commonly used utilities that comes as a core command installed on almost every UNIX and Linux-based operating system.The vulnerability in question is a sudo security policy bypass issue that could allow a malicious user or a program to execute arbitrary commands as … [Read more...] about Sudo Flaw Lets Linux Users Run Commands As Root Even When They’re Restricted