As the volume and complexity of cyber threats continue to increase, security analysts face mounting pressure to protect their organizations from attack with maximum efficiency. Elastic Security 8.8 introduces features designed to help analysts digest, prioritize, and quickly respond to security incidents. These features include the following:The improved alert triage … [Read more...] about Elastic Security 8.8: Powerful endpoint response, alert triage, and data accuracy to bring more efficiency to security
security
What to Look for When Selecting a Static Application Security Testing (SAST) Solution
If you're involved in securing the applications your organization develops, there is no question that Static Application Security Testing (SAST) solutions are an important part of a comprehensive application security strategy. SAST secures software, supports business more securely, cuts down on costs, reduces risk, and speeds time to development, delivery, and deployment of … [Read more...] about What to Look for When Selecting a Static Application Security Testing (SAST) Solution
Industrial control systems security with Elastic Security and Zeek
Keeping track of all ICS asset history and accurate status in a global inventory is critical not only for purposes like maintenance, cost management, and environment optimization but also for the system's security. Well-implemented and maintained inventories are key to ICS security programs, since you can’t protect what you don’t know about. Knowing what is on the ICS network, … [Read more...] about Industrial control systems security with Elastic Security and Zeek
Increasing Implications: Adding Security Analysis to Kubernetes 360 Platform
A quick look at headlines emanating from this year’s sold out KubeCon + CloudNativeCon Europe underlines the fact that Kubernetes security has risen to the fore among practitioners and vendors alike.As is typically the case with our favorite technologies, we’ve reached that point where people are determined to ensure security measures aren’t “tacked on after the fact” as … [Read more...] about Increasing Implications: Adding Security Analysis to Kubernetes 360 Platform
Cisco and VMware Release Security Updates to Patch Critical Flaws in their Products
Apr 21, 2023Ravie LakshmananSoftware Update / Network Security Cisco and VMware have released security updates to address critical security flaws in their products that could be exploited by malicious actors to execute arbitrary code on affected systems. The most severe of the vulnerabilities is a command injection flaw in Cisco Industrial Network Director (CVE-2023-20036, … [Read more...] about Cisco and VMware Release Security Updates to Patch Critical Flaws in their Products
The importance of a unified observability solution in security implementation
Observability is critical for effective security implementation. It allows organizations to monitor their systems, applications, and networks in real-time; detect and investigate security incidents; and quickly respond to them. But having multiple tools and solutions for observability can create a fragmented view of the environment, making it difficult to gain a comprehensive … [Read more...] about The importance of a unified observability solution in security implementation
Four top tips for blockchain asset security
Cryptocurrencies and other blockchain assets aren’t protected by bank guarantees or other “traditional” financial security measures. Therefore, investors need to take every possible precaution to protect themselves. Here are four key tips for storing cryptocurrencies securely and protecting other cryptoassets. 1. Expect scams The variety of different cryptoassets combined with … [Read more...] about Four top tips for blockchain asset security
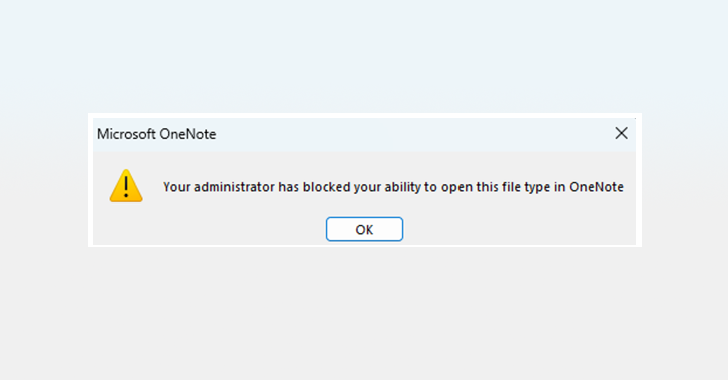
Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Up until now, users were shown a dialog warning them that opening such attachments could harm their computer and data, but it was possible to dismiss the prompt and open the … [Read more...] about Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Evades Macro Security via OneNote Attachments
Mar 20, 2023Ravie LakshmananEndpoint Security / Email Security The notorious Emotet malware, in its return after a short hiatus, is now being distributed via Microsoft OneNote email attachments in an attempt to bypass macro-based security restrictions and compromise systems. Emotet, linked to a threat actor tracked as Gold Crestwood, Mummy Spider, or TA542, continues to be a … [Read more...] about Evades Macro Security via OneNote Attachments
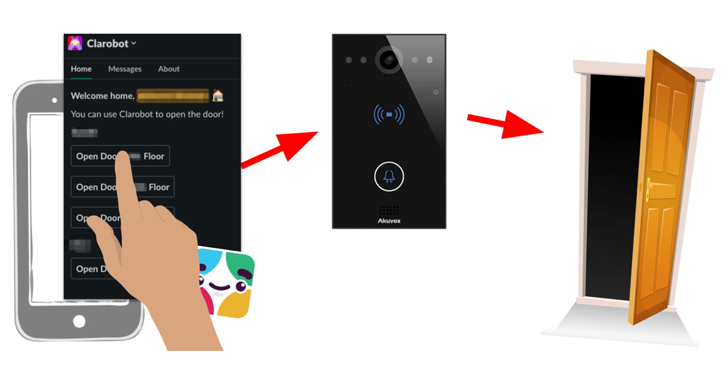
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
Mar 13, 2023Ravie LakshmananEnterprise Security / Privacy More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty … [Read more...] about Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom