It's no secret that data leaks have become a major concern for both citizens and institutions across the globe. They can cause serious damage to an organization's reputation, induce considerable financial losses, and even have serious legal repercussions. From the infamous Cambridge Analytica scandal to the Equifax data breach, there have been some pretty high-profile leaks … [Read more...] about Are Your APIs Leaking Sensitive Data?
the hacker news
User Sign-Ups and Package Uploads Temporarily Halted
May 21, 2023Ravie LakshmananSoftware Security / Malware The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have temporarily disabled the ability for users to sign up and upload new packages until further notice. "The volume of malicious users and malicious projects being created on the index in the … [Read more...] about User Sign-Ups and Package Uploads Temporarily Halted
Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
May 20, 2023Ravie LakshmananCyber Crime / Ransomware The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021. Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest. "In these recent … [Read more...] about Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
May 19, 2023Ravie LakshmananArtificial Intelligence / Cyber Threat Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. "Both AI services are extremely popular but lack first-party standalone apps (i.e., users … [Read more...] about Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
How to Reduce Exposure on the Manufacturing Attack Surface
Digitalization initiatives are connecting once-isolated Operational Technology (OT) environments with their Information Technology (IT) counterparts. This digital transformation of the factory floor has accelerated the connection of machinery to digital systems and data. Computer systems for managing and monitoring digital systems and data have been added to the hardware and … [Read more...] about How to Reduce Exposure on the Manufacturing Attack Surface
Serious Unpatched Vulnerability Uncovered in Popular Belkin Wemo Smart Plugs
May 17, 2023Ravie LakshmananInternet of Things / Vulnerability The second generation version of Belkin's Wemo Mini Smart Plug has been found to contain a buffer overflow vulnerability that could be weaponized by a threat actor to inject arbitrary commands remotely. The issue, assigned the identifier CVE-2023-27217, was discovered and reported to Belkin on January 9, 2023, by … [Read more...] about Serious Unpatched Vulnerability Uncovered in Popular Belkin Wemo Smart Plugs
Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
May 16, 2023Ravie LakshmananEndpoint Security / Cyber Threat A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems. The findings come from SentinelOne, which observed an uptick in the number of Geacon payloads appearing on VirusTotal in recent months. "While some of these are likely … [Read more...] about Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
Researchers Uncover Powerful Backdoor and Custom Implant in Year-Long Cyber Campaign
May 15, 2023Ravie LakshmananCyber Threat / Malware Government, aviation, education, and telecom sectors located in South and Southeast Asia have come under the radar of a new hacking group as part of a highly-targeted campaign that commenced in mid-2022 and continued into the first quarter of 2023. Symantec, by Broadcom Software, is tracking the activity under its … [Read more...] about Researchers Uncover Powerful Backdoor and Custom Implant in Year-Long Cyber Campaign
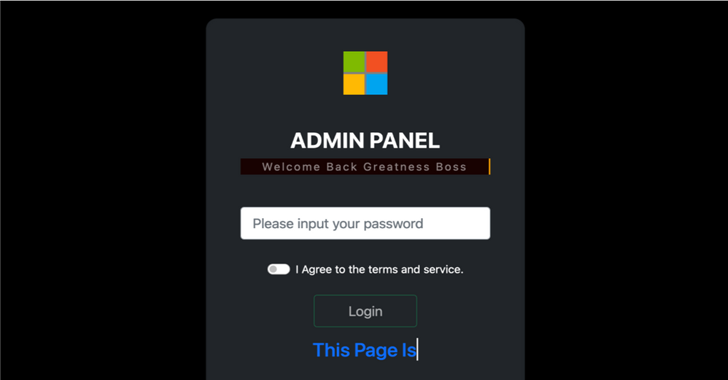
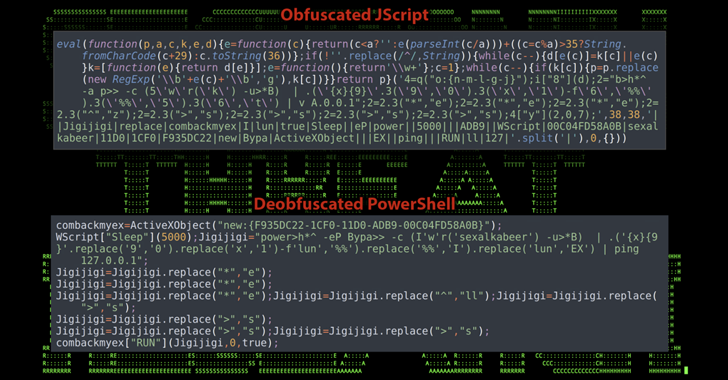
New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing Phishing Pages
May 13, 2023Ravie Lakshmanan A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to target business users of the Microsoft 365 cloud service since at least mid-2022, effectively lowering the bar to entry for phishing attacks. "Greatness, for now, is only focused on Microsoft 365 phishing pages, providing its affiliates … [Read more...] about New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing Phishing Pages
XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks
May 12, 2023Ravie LakshmananCyber Threat / Malware Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare … [Read more...] about XWorm Malware Exploits Follina Vulnerability in New Wave of Attacks