Credential theft is clearly still a problem. Even after years of warnings, changing password requirements, and multiple forms of authentication, password stealing remains a top attack method used by cyber criminals. The latest report from the Ponemon Institute shares that 54% of security incidents were caused by credential theft, followed by ransomware and DDoS attacks. 59% of … [Read more...] about Credential Theft Is (Still) A Top Attack Method
the hacker news
Tornado Cash Developer Arrested After U.S. Sanctions the Cryptocurrency Mixer
Dutch authorities on Friday announced the arrest of a software developer in Amsterdam who is alleged to be working for Tornado Cash, days after the U.S. sanctioned the decentralized crypto mixing service. The 29-year-old individual is "suspected of involvement in concealing criminal financial flows and facilitating money laundering" through the service, the Dutch Fiscal … [Read more...] about Tornado Cash Developer Arrested After U.S. Sanctions the Cryptocurrency Mixer
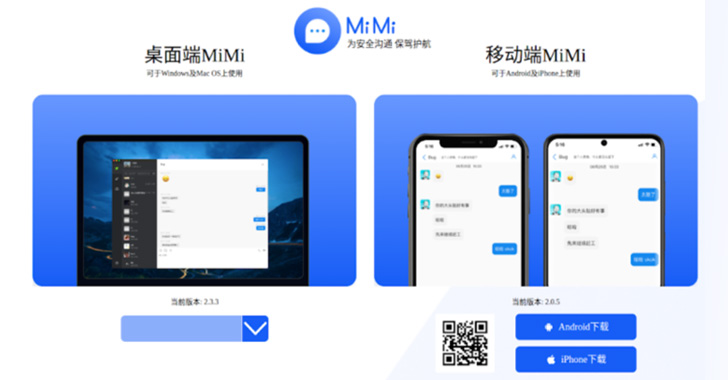
Chinese Hackers Backdoored MiMi Chat App to Target Windows, Linux, macOS Users
A pair of reports from cybersecurity firms SEKOIA and Trend Micro sheds light on a new campaign undertaken by a Chinese threat actor named Lucky Mouse that involves leveraging a trojanized version of a cross-platform messaging app to backdoor systems. Infection chains leverage a chat application called MiMi, with its installer files compromised to download and install HyperBro … [Read more...] about Chinese Hackers Backdoored MiMi Chat App to Target Windows, Linux, macOS Users
Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
A security feature bypass vulnerability has been uncovered in three signed third-party Unified Extensible Firmware Interface (UEFI) boot loaders that allow bypass of the UEFI Secure Boot feature. "These vulnerabilities can be exploited by mounting the EFI System Partition and replacing the existing bootloader with the vulnerable one, or modifying a UEFI variable to load the … [Read more...] about Researchers Uncover UEFI Secure Boot Bypass in 3 Microsoft Signed Boot Loaders
Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Three different offshoots of the notorious Conti cybercrime cartel have resorted to the technique of call-back phishing as an initial access vector to breach targeted networks. "Three autonomous threat groups have since adopted and independently developed their own targeted phishing tactics derived from the call back phishing methodology," cybersecurity firm AdvIntel said in a … [Read more...] about Conti Cybercrime Cartel Using ‘BazarCall’ Phishing Attacks as Initial Attack Vector
Former Twitter Employee Found Guilty of Spying for Saudi Arabia
A former Twitter employee has been pronounced guilty for his role in digging up private information pertaining to certain Twitter users and turning over that data to Saudi Arabia. Ahmad Abouammo, 44, was convicted by a jury after a two-week trial in San Francisco federal court, Bloomberg reported Tuesday. He faces up to 20 years in prison when sentenced. The verdict comes … [Read more...] about Former Twitter Employee Found Guilty of Spying for Saudi Arabia
Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing Attack
Customer engagement platform Twilio on Monday disclosed that a "sophisticated" threat actor gained "unauthorized access" using an SMS-based phishing campaign aimed at its staff to gain information on a "limited number" of accounts. The social-engineering attack was bent on stealing employee credentials, the company said, calling the as-yet-unidentified adversary … [Read more...] about Twilio Suffers Data Breach After Employees Fall Victim to SMS Phishing Attack
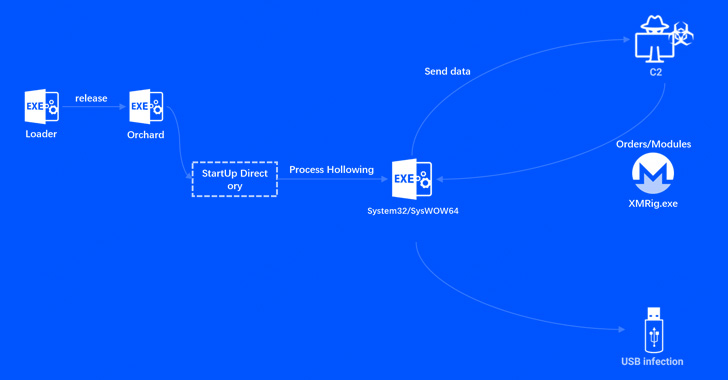
New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
A new botnet named Orchard has been observed using Bitcoin creator Satoshi Nakamoto's account transaction information to generate domain names to conceal its command-and-control (C2) infrastructure. "Because of the uncertainty of Bitcoin transactions, this technique is more unpredictable than using the common time-generated [domain generation algorithms], and thus more … [Read more...] about New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
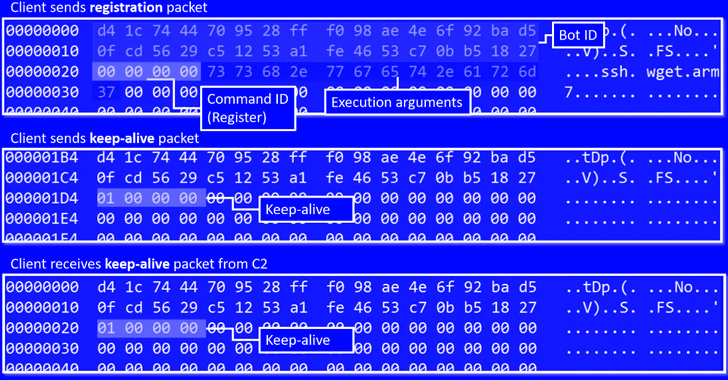
New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack
A new IoT botnet malware dubbed RapperBot has been observed rapidly evolving its capabilities since it was first discovered in mid-June 2022. "This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented … [Read more...] about New IoT RapperBot Malware Targeting Linux Servers via SSH Brute-Forcing Attack
Hackers Exploit Twitter Vulnerability to Exposes 5.4 Million Accounts
Twitter on Friday revealed that a now-patched zero-day bug was used to link phone numbers and emails to user accounts on the social media platform. "As a result of the vulnerability, if someone submitted an email address or phone number to Twitter's systems, Twitter's systems would tell the person what Twitter account the submitted email addresses or phone number was associated … [Read more...] about Hackers Exploit Twitter Vulnerability to Exposes 5.4 Million Accounts