The threat landscape is full of moving targets. Over time, popular tools, tactics, and procedures change. Malicious techniques fall out of fashion, only to come roaring back months, if not years, later. All the while, security practitioners monitor network traffic and adapt their defenses to protect their users and networks. Keeping on top of these trends is one of the most … [Read more...] about How to Monitor Network Traffic: Findings from the Cisco Cyber Threat Trends Report
Threat
Integration of Cisco Secure Threat Defense Virtual with Megaport
Business critical data can originate from diverse sources ranging from multiple public clouds, private clouds, and internal servers to a remote employee’s device. Securing each data entity individually is time consuming and challenging due to lack of compliance between all the data points. With the increase in such use cases, you must be able to deploy the firewall quickly and … [Read more...] about Integration of Cisco Secure Threat Defense Virtual with Megaport
AI-Powered Threat Hunting for Cybersecurity Pros (Webinar)
May 10, 2024The Hacker NewsArtificial Intelligence / Threat Hunting Artificial intelligence (AI) is transforming cybersecurity, and those leading the charge are using it to outsmart increasingly advanced cyber threats. Join us for an exciting webinar, "The Future of Threat Hunting is Powered by Generative AI," where you'll explore how AI tools are shaping the future of … [Read more...] about AI-Powered Threat Hunting for Cybersecurity Pros (Webinar)
Threat Actors Can Leverage AWS STS to Infiltrate Cloud Accounts
Dec 06, 2023NewsroomAccess Management / Cloud Security Threat actors can take advantage of Amazon Web Services Security Token Service (AWS STS) as a way to infiltrate cloud accounts and conduct follow-on attacks. The service enables threat actors to impersonate user identities and roles in cloud environments, Red Canary researchers Thomas Gardner and Cody Betsworth said in a … [Read more...] about Threat Actors Can Leverage AWS STS to Infiltrate Cloud Accounts
New Emerging APT Threat Exploiting WinRAR Flaw
Nov 16, 2023NewsroomAdvanced Persistent Threat / Zero-Day A hacking group that leveraged a recently disclosed security flaw in the WinRAR software as a zero-day has now been categorized as an entirely new advanced persistent threat (APT). Cybersecurity company NSFOCUS has described DarkCasino as an "economically motivated" actor that first came to light in 2021. "DarkCasino … [Read more...] about New Emerging APT Threat Exploiting WinRAR Flaw
Okta’s Support System Breach Exposes Customer Data to Unidentified Threat Actors
Oct 21, 2023NewsroomData Breach / Cyber Attack Identity services provider Okta on Friday disclosed a new security incident that allowed unidentified threat actors to leverage stolen credentials to access its support case management system. "The threat actor was able to view files uploaded by certain Okta customers as part of recent support cases," David Bradbury, Okta's … [Read more...] about Okta’s Support System Breach Exposes Customer Data to Unidentified Threat Actors
The Interdependence between Automated Threat Intelligence Collection and Humans
The volume of cybersecurity vulnerabilities is rising, with close to 30% more vulnerabilities found in 2022 vs. 2018. Costs are also rising, with a data breach in 2023 costing $4.45M on average vs. $3.62M in 2017. In Q2 2023, a total of 1386 victims were claimed by ransomware attacks compared with just 831 in Q1 2023. The MOVEit attack has claimed over 600 victims so far and … [Read more...] about The Interdependence between Automated Threat Intelligence Collection and Humans
Identity Threat Detection & Response (ITDR) – Rips in Your Identity Fabric
Sep 13, 2023The Hacker NewsThreat Detection / SaaS Security In today's digital age, SaaS applications have become the backbone of modern businesses. They streamline operations, enhance productivity, and foster innovation. But with great power comes great responsibility. As organizations integrate more SaaS applications into their workflows, they inadvertently open the door to … [Read more...] about Identity Threat Detection & Response (ITDR) – Rips in Your Identity Fabric
Learn How Your Business Data Can Amplify Your AI/ML Threat Detection Capabilities
Aug 25, 2023The Hacker NewsThreat Detection / Artificial Intelligence In today's digital landscape, your business data is more than just numbers—it's a powerhouse. Imagine leveraging this data not only for profit but also for enhanced AI and Machine Learning (ML) threat detection. For companies like Comcast, this isn't a dream. It's reality. Your business comprehends its … [Read more...] about Learn How Your Business Data Can Amplify Your AI/ML Threat Detection Capabilities
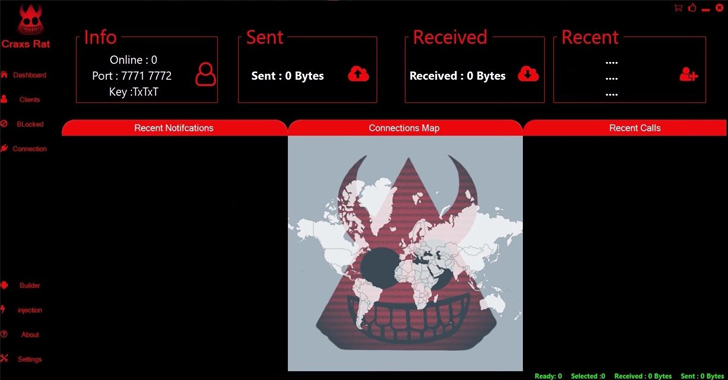
Syrian Threat Actor EVLF Unmasked as Creator of CypherRAT and CraxsRAT Android Malware
Aug 23, 2023THNMobile Security / Cyber Crime A Syrian threat actor named EVLF has been outed as the creator of malware families CypherRAT and CraxsRAT. "These RATs are designed to allow an attacker to remotely perform real-time actions and control the victim device's camera, location, and microphone," Cybersecurity firm Cyfirma said in a report published last week. CypherRAT … [Read more...] about Syrian Threat Actor EVLF Unmasked as Creator of CypherRAT and CraxsRAT Android Malware