Think about all the data behind projects like defense intelligence, public health records, urban planning models, and more. Government agencies are generating enormous quantities of data all the time. Things get even more tricky when the data is spread across cloud platforms, on-prem systems, or specialized environments like satellites and emergency response centers. It’s hard … [Read more...] about Understanding data mesh in public sector: Pillars, architecture, and examples
Understanding
Understanding the Quantum Threat to Network Security
Confidentiality is a fundamental pillar of information security. In sensitive deployments, such as those involving federal governments, military and defense agencies, and large financial institutions, the demand for confidentiality extends well beyond the typical 5 to 10 years, often reaching 20 years or more. The same also applies to telecom operators and … [Read more...] about Understanding the Quantum Threat to Network Security
Machine learning vs. AI: Understanding the differences
Despite the terms often being used interchangeably, machine learning and AI are separate and distinct concepts. As we’ve already mentioned, machine learning is a type of AI, but not all AI is, or uses, machine learning. Even though there is a large amount of overlap (more on that later), they often have different capabilities, objectives, and scope.The broader aim of AI is to … [Read more...] about Machine learning vs. AI: Understanding the differences
Understanding AI search algorithms | Elastic Blog
NLP algorithms are an essential part of search because they bridge the gap between human communication and machine understanding. This enables search AI to understand what is being asked of it and to deliver results that are relevant and contextual to the query.Using NLP, the search results will be more aligned with the user's intent, and the algorithm will be able to handle … [Read more...] about Understanding AI search algorithms | Elastic Blog
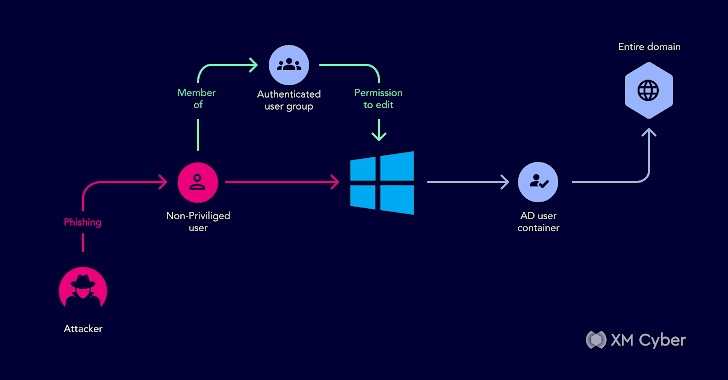
Understanding Active Directory Attack Paths to Improve Security
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a'changin' – and a few years back, Microsoft introduced Azure Active … [Read more...] about Understanding Active Directory Attack Paths to Improve Security
Mastering API Security: Understanding Your True Attack Surface
Jun 13, 2023The Hacker NewsAPI Security / Webinar Believe it or not, your attack surface is expanding faster than you realize. How? APIs, of course! More formally known as application programming interfaces, API calls are growing twice as fast as HTML traffic, making APIs an ideal candidate for new security solutions aimed at protecting customer data, according to … [Read more...] about Mastering API Security: Understanding Your True Attack Surface
Understanding Business Email Compromise to better protect against it
What is business email compromise? Imagine this: Your CEO sends you an email asking for your help transferring $5,000 to a new vendor for an urgent project. You make the transfer, only to find out later that the email was actually from an imposter, and that money is now in the hands of cybercriminals. Oops, right? crickets Business Email Compromise (BEC) is a type of cybercrime … [Read more...] about Understanding Business Email Compromise to better protect against it